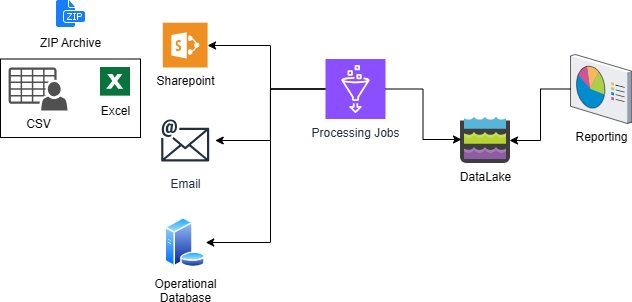
In this episode of Public Sector Podcast, we dive into the Government Accountability Office (GAO) and its role in overseeing federal cybersecurity with a focus on Zero Trust Architecture (ZTA). Our guest, Jennifer Franks, Director of the Center for Enhanced Cybersecurity and Analytics Foundry at GAO, shares insights into GAO’s cybersecurity strategy, the challenges of securing federal information systems, and the importance of Zero Trust Architecture in protecting sensitive government data.
What is the Government Accountability Office (GAO)?
The Government Accountability Office (GAO) is a non-partisan, fact-based oversight agency that ensures efficient spending of taxpayer dollars across the federal government. Established over 103 years ago, GAO acts as a watchdog for government operations, promoting transparency and accountability.
- Mission and Purpose: GAO evaluates the effectiveness of federal programs, ensuring government agencies spend taxpayer money efficiently and responsibly.
- Cybersecurity Oversight: Cybersecurity has been on GAO’s High-Risk List since 1997, highlighting the growing importance of protecting federal information systems and critical infrastructure.
- Focus Areas: GAO’s cybersecurity oversight focuses on securing federal information systems, safeguarding critical infrastructure, and protecting privacy and sensitive data.
Implementing Zero Trust Architecture (ZTA) in Federal Cybersecurity
Zero Trust Architecture (ZTA) is a strategic cybersecurity approach that eliminates implicit trust by enforcing continuous verification, least privilege access, and real-time monitoring.
- What is Zero Trust Architecture? ZTA ensures that no entity—user, device, or network component—is trusted by default. It requires continuous identity authentication and authorisation checks to access sensitive data.
- Removing Implicit Trust: Unlike traditional perimeter-based security models, ZTA removes implicit trust, ensuring that all users and devices are continuously verified.
- Continuous Verification: ZTA’s approach includes least privilege access, ensuring users only have access to the data they need while preventing unauthorised access and potential data breaches.
Challenges in Federal Cybersecurity and Inventory Management
One of the biggest challenges in federal cybersecurity is inventory management, especially in identifying unknown data sources and untracked system connections.
- Inventory Management Gap: Federal agencies struggle with inventory management, making it difficult to track and monitor data sources, devices, and network assets.
- Continuous Monitoring and Access Control: Effective ZTA implementation requires continuous monitoring and strict access control to detect vulnerabilities and manage risks.
- Data and Device Visibility: Organisations must catalog and continuously monitor their data, devices, and network assets to maintain a comprehensive security posture.
Educational Awareness and Continuous Security Training
Security awareness is critical to the success of Zero Trust Architecture and overall cybersecurity strategy. GAO promotes continuous education and training for federal employees to stay updated on evolving threats.
- Continuous Security Training: Unlike traditional annual security training, GAO is moving towards continuous awareness training, including monthly updates for cybersecurity personnel and quarterly training for all enterprise-connected individuals.
- Risk Awareness and Adaptation: Continuous training ensures that employees are aware of the latest cybersecurity threats and vulnerabilities and are equipped to respond to evolving risks.
- Human Element in Cybersecurity: By educating employees on best practices, GAO ensures human error is minimised in cybersecurity incidents.
Looking Ahead: The Future of Zero Trust Architecture and Cybersecurity
Zero Trust Architecture is a continuously evolving cybersecurity model that adapts to emerging threats and vulnerabilities. GAO emphasises that ZTA is a marathon, not a sprint, requiring continuous improvement and adaptation.
- Phased Implementation: GAO recommends a phased approach to ZTA implementation, starting with the most high-risk systems and gradually expanding to other areas.
- Legacy Systems and Modernisation: One of the challenges in ZTA adoption is integrating legacy systems with modern security protocols.
- Continuous Evolution: GAO stresses the importance of continuous technological evolution to respond to new cybersecurity threats, stating that cybersecurity is a never-ending journey.
Key Takeaways
- Zero Trust Architecture: ZTA eliminates implicit trust, ensuring continuous verification of users and devices for enhanced cybersecurity.
- Inventory Management and Access Control: Effective ZTA implementation requires comprehensive inventory management and continuous monitoring of data and network assets.
- Continuous Education and Awareness: GAO promotes ongoing cybersecurity training to keep federal employees informed about evolving threats and best practices.
- Phased Approach and Continuous Evolution: Zero Trust is a marathon, not a sprint, requiring continuous improvement and adaptation to new cybersecurity threats.
Join us as we explore how the Government Accountability Office is redefining cybersecurity with Zero Trust Architecture and ensuring the protection of federal information systems against evolving cyber threats.