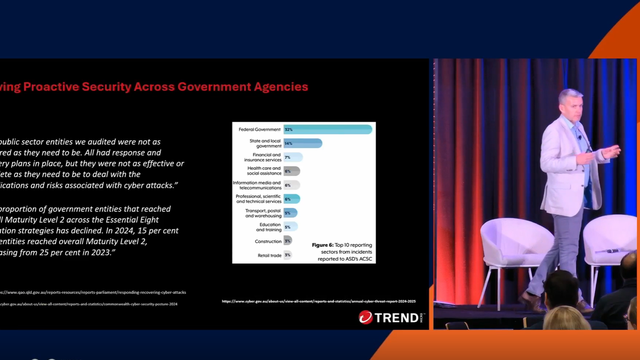
The last few years in Australia have been some of the most active and visible in terms of cyber threats and cyber-attacks. Almost no industry and no company has been left immune, with the size of the company and the size and sophistication of the IT department seemingly no barrier for determined hackers or threat actors with significant resources. With large, expensive and very impactful breaches at Optus and Medibank, to name just two of the biggest, no organisation can feel completely secure, and in fact, most IT professionals agree that future similar scale attacks are likely. The question generally is not if but when. This is so much the case that agencies all over Australia are taking unprecedented steps to protect themselves and their data, but even the best laid plans do not always produce results.
Email Fixes to Mitigate Phishing
Although the majority of threats will likely always come from malicious or criminal sources, the latest data from a report published by the Office of the Australian Information Commissioner for the second half of 2022, suggests that up to a quarter stem from human error. The vast majority of these are emails sent to the wrong recipient, unauthorised release of information, or a failure to BCC when sending an email. Moreover, phishing continues to be a constant threat. This is largely because the biggest dangers are often caused by the simplest of mistakes, and are actually relatively easy to control if people paid more attention. The data says that not only are most of these breaches in the late afternoon when people are tired, but many of them are caused by applications that are supposed to make things easier, like the Outlook autocomplete naming function. Simply turning such functions off can be the simplest fix and will force people to be more attentive.
Shared Responsibility
In general, the attacks that often cause the greatest damage are not the clever applications with lots of coding, but the less sophisticated ones such as fairly uncomplicated impersonation attacks. Many institutions have measures in place to counter these attacks, but sometimes they are only for senior staff since they are often the ones most at risk, though it is the junior staff who are much more vulnerable and unaware of what to look out for, and that is what the attackers prey on. In fact, junior or entry level staff are rarely consulted when it comes to cyber protection or many other matters, yet in the case of cyber security, it should always be a shared responsibility.
Mandatory Reporting Legislation
As part of that shared responsibility, the Commonwealth already has mandatory data breach reporting legislation, and other states are about to implement such legislation, or are in the process of drafting it for their own jurisdictional needs. One of the reasons for doing so is that data is constantly being sold with millions of stolen credentials being used for nefarious purposes. This was highlighted recently during the breach at Optus, where some people had to get new IDs or other credentials, causing great inconvenience, but it could have been a lot worse. Mandatory reporting will not solve all the problems and will certainly not prevent all the causes of human error, but it may reduce some of the risk, it will likely assist in stemming the breach as quickly as possible, and it should be able to prevent some of the harm, both in terms of resources and to people.
Cyber Vigilant Cultures for All
Ultimately, every incident, whenever and wherever it occurs is a learning opportunity. However, dealing with cyber-attacks is usually a reactive process. Organisations in general need to become more proactive. One of the reasons why phishing is on the rise is because the attackers know that a vast number of people ignore the basics, like MFA, patching and so many other cyber hygiene factors. Everyone, no matter their role in the organisation, should be a cyber warrior and part of the solution. One way of embedding that is through incident training and maybe even gamifying the process to make the training more fun, more competitive and therefore hopefully more ingrained. This is really about creating a culture of cyber security and cyber vigilance, so that those things are seen as being a necessity not a hindrance. The best kind of people to work in IT are not those just with technical skills, but are curious people who know how to explain to others why cyber protection is so important.
Taken together, all of these elements are designed to eliminate as much human error as is feasible and to embed constant vigilance as a form of mitigation, which in turn is good for overall cyber security across all organisations and across the country.