Two Decades On: Rethinking Active Directory Defence for a High-Threat Era
Explore how government IT and security leaders can modernise Active Directory defences to proactively counter evolving cyber threats, meet regulatory demands, and safeguard critical services across hybrid environments.
For over 20 years, Active Directory has been the foundation of identity management across the public sector. But as government agencies face increasingly sophisticated cyber threats and rising regulatory obligations—including privacy law reforms and the evolving guidance from the Australian Signals Directorate (ASD)—traditional approaches to AD protection are no longer enough.
This webinar brings together senior IT and security leaders to explore how governments can modernise identity protection strategies across hybrid, on-premises and cloud environments. With operational continuity, critical infrastructure protection and citizen trust on the line, it’s time to elevate AD defence from reactive recovery to proactive risk prevention.
Key discussion points include:
- What “modern defence” really means for Active Directory in a post-ransomware, zero-trust environment
- How to apply ASD Essential Eight, IRAP controls and identity-specific recommendations at scale
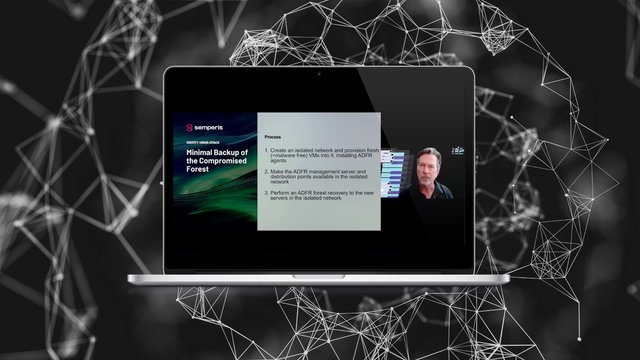
- Streamlining incident response and audit-readiness with advanced AD recovery and change monitoring
- Minimising service disruption and data loss through secure, tested recovery frameworks
- Enabling visibility and accountability across increasingly complex identity ecosystems
This is a critical conversation for CIOs, CISOs, infrastructure leaders and directors responsible for safeguarding government systems, data and services. Attendees will walk away with actionable insights to strengthen identity resilience and prepare for what’s next in cyber defence.
Facilitators:

James Duncan
Technical Director, Government Uplift, Australian Signals Directorate

Peter Gigengack
Director Cyber Security, Office of Digital Government, Department of the Premier and Cabinet, WA
Recommendations

South Australia’s Industry Participation Policy

6 questions to ask before investing in meeting room solutions
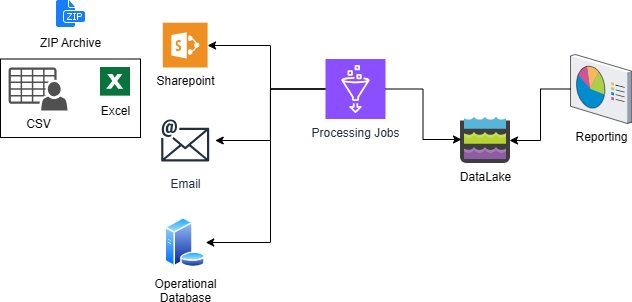
Modern Data Platform: a viable alternative to traditional data warehouse architectures

Overcoming Challenges in IT Modernization Projects